Introduction
- Server-Side Encryption with Customer Provided Keys (SSE-C)
- Server-Side Encryption with S3-Managed Keys (SSE-S3)
- Server-Side Encryption with KMS Keys (SSE-KMS)
Server-Side Encryption with Customer Provided Keys
With this method, you take control of key management by supplying S3 with the data in plain text and an encryption key. S3 then uses this key to encrypt the data, storing both the ciphertext of the encrypted object and a hash of the key. The key itself is securely destroyed.
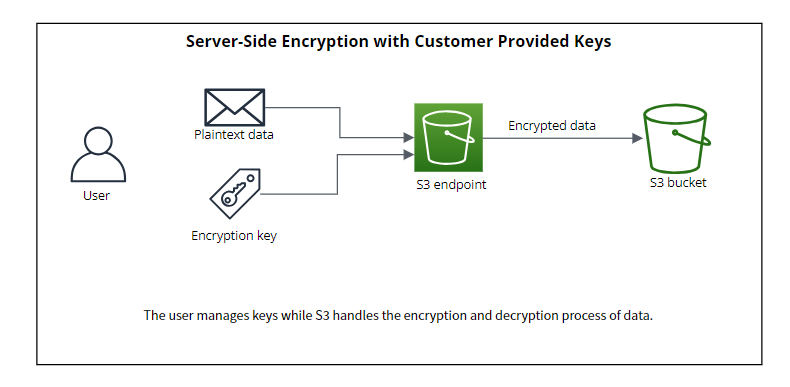
to decrypt the object, you must provide S3 with the key. S3 will verify if the provided key is correct and, if successful, decrypt the object, returning the plaintextand descards the key. This approach empowers users to handle the encryption keys, adding an extra layer of control over data security.
Server-Side Encryption with S3-Managed Keys
With this method S3 handles the both processes : managing the keys and encrypt/decrypt the data and it is the default method that S3 uses. You just need to provide the plaintext data and S3 will creates, manages and rotates the key so you have zero control of the key.
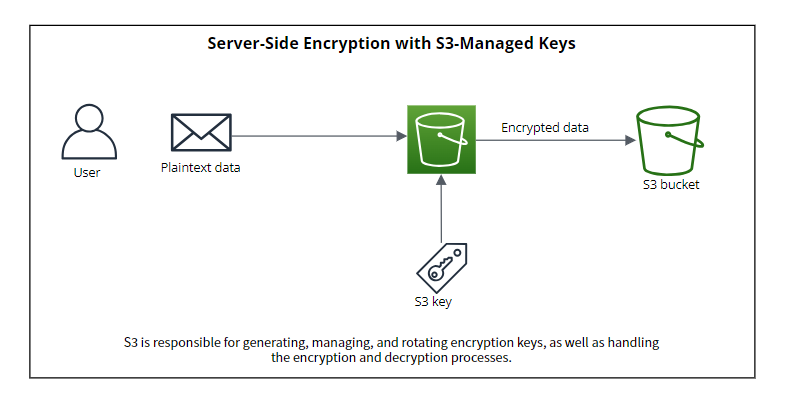
SSE-S3 uses the Advanced Encryption Standard (AES) algorithm with a key size of 256 bits. AES-256 is a widely adopted encryption standard known for its strength and security. When you retrieve an object from an SSE-S3 encrypted bucket, Amazon S3 automatically decrypts the object before returning it to the requester. As a user, you do not need to perform any additional steps to decrypt the data.
There is no additional cost for using SSE-S3. It is included as part of the standard Amazon S3 service offerings but there is a significant drawback associated with this method, primarily related to Role Separation. Since everyone with access to S3 possesses the ability to read encrypted data, it raises concerns about data privacy and security. In many scenarios, you may want to restrict access to encrypted data to specific individuals or roles within your organization.
Server-Side Encryption with KMS Keys
With this approach, another AWS service involved in the process is AWS Key Management Service (KMS). KMS is responsible for managing keys with role separation. In order to use a specific key generated by KMS, you need to have permissions and these controlled by IAM (Identity and Access Management).
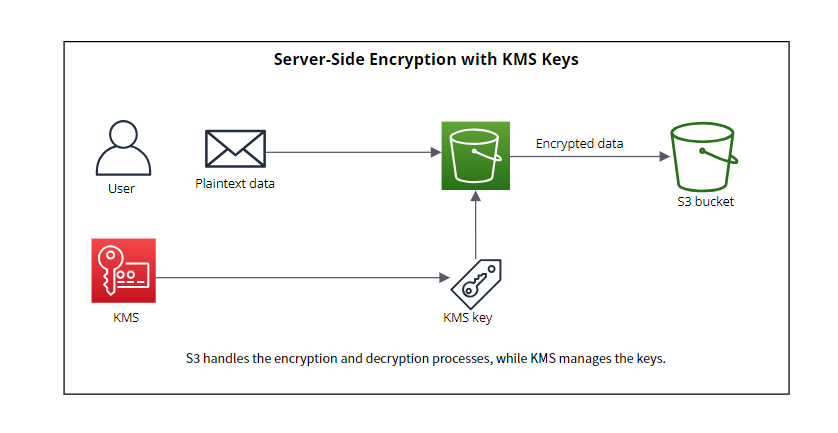
In this case, S3 will solely handle the encryption and decryption processes, while KMS will manage the keys with isolated permissions that are configurable by you. Each time S3 requests a key from KMS to encrypt specific data, KMS will provide both a Plaintext key and a Ciphertext version of the encryption key (DEK). S3 will use the plaintext version of the key for encryption, then discard it and store the ciphertext version along with the encrypted data for later use in the decryption process.
Conclusion
S3 server-side encryption offers three methods: SSE-C, SSE-S3, and SSE-KMS, each tailored to diverse encryption needs. SSE-C empowers users with key management control, while SSE-S3 streamlines encryption with automated key management. However, SSE-S3 poses concerns about role separation, as it grants universal access to encrypted data. In contrast, SSE-KMS enhances security by leveraging AWS KMS for key management, ensuring customizable permissions and role separation.
