Introduction
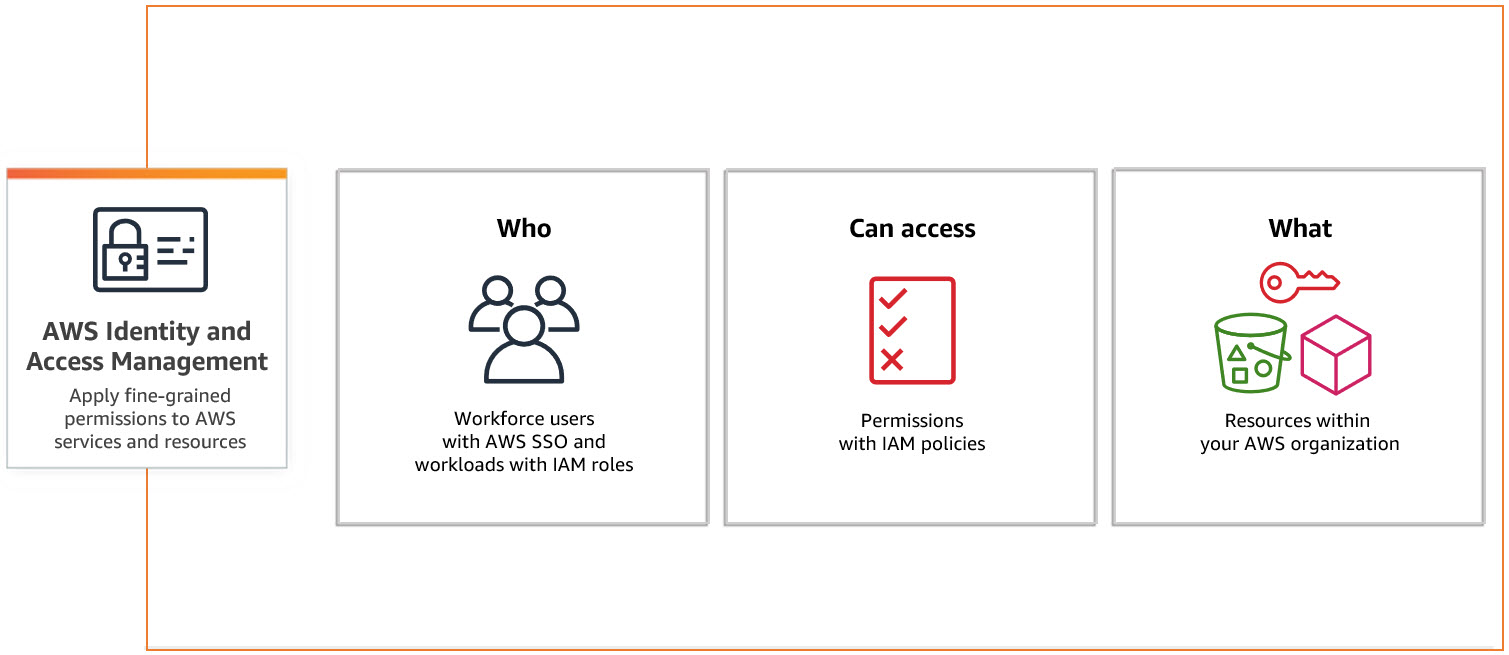
When users seek to perform actions on resources, such as creating an EC2 instance, specific permissions are required. IAM empowers the creation of users and enables precise control over permissions and authorizations through IAM policies.
An IAM User is designated as an identity, and the system introduces two additional identity types: Roles and Groups. These identities provide enhanced flexibility in access management, offering a comprehensive approach to permissions and organizational control.
IAM Image
IAM Policies
An IAM Policy serves as a mechanism to either grant or deny permissions to identities within the AWS environment. These policies, presented in JSON or YAML format, are linked to specific identities.
Once a policy is attached, the associated identity operates strictly within the boundaries defined by the policy. Here's a simple example of an IAM Policy:
IAM Image
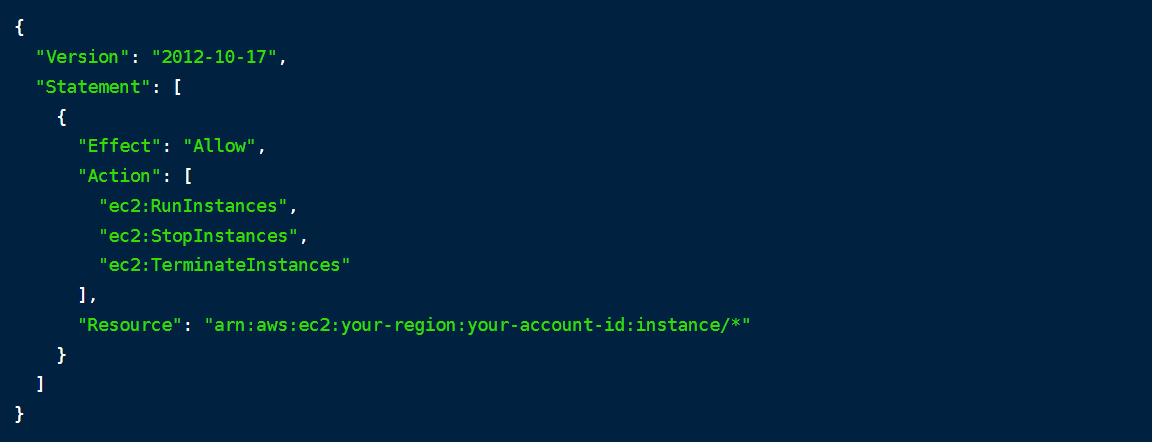
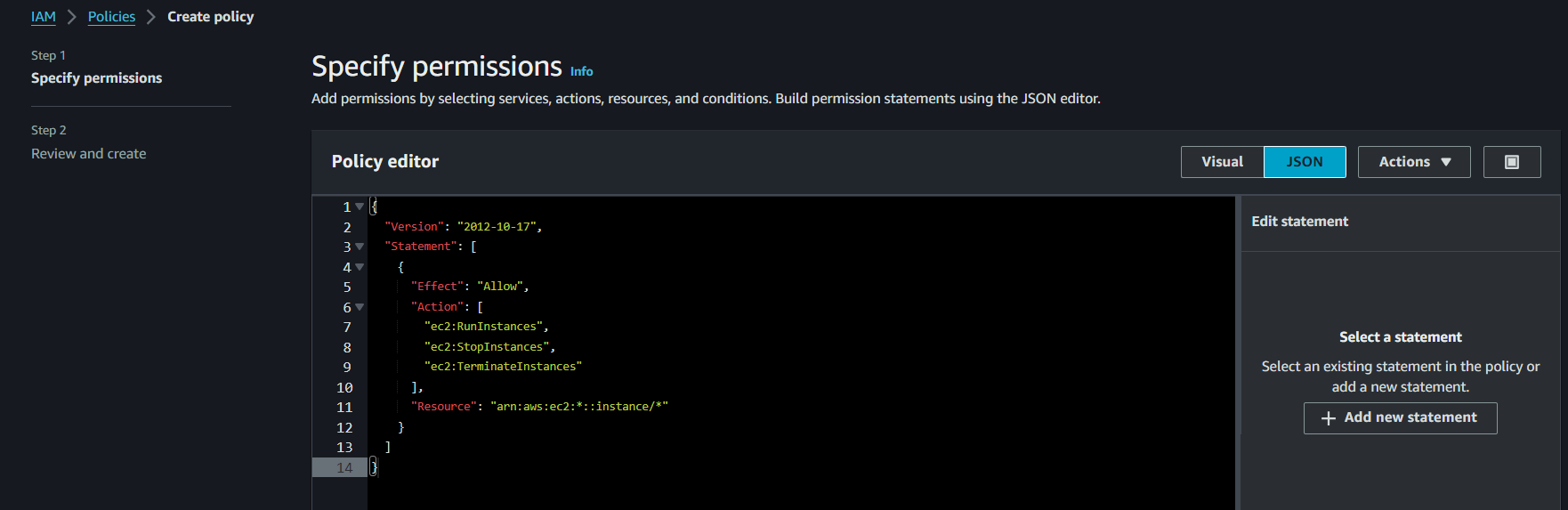
In this example, we create an IAM Policy that grants create, stop, and terminate EC2 instances:
- Version: This specifies the version of the IAM policy language. In this case, it's set to "2012-10-17," which is a standard version.
- Statement: This is an array of policy statements. Each statement in the array represents a set of permissions.
- Effect: This indicates that the specified actions are allowed. You could also use "Effect": "Deny" to explicitly deny the actions.
- Action: This lists the AWS actions that are allowed. In this case, the policy allows the actions of running, stopping, and terminating EC2 instances.
- Resource: This specifies the resource to which the actions apply. Replace your-region with the AWS region code where your instances reside, and replace your-account-id with your AWS account ID. The instance/* at the end indicates that these permissions apply to all EC2 instances (* is a wildcard for any instance ID).
In this example, we are granting permissions specifically for handling EC2 instances. It's important to note that, in IAM, the order of evaluation follows a specific sequence: Explicit Deny, Explicit Allow, and finally, Implicit Deny. This means that if an action is not explicitly allowed for EC2 instances, it will implicitly be denied. Careful attention to this order is crucial for crafting policies to ensure that only intended actions are permitted, and that security measures are in place.
Evaluate multiple policies
Explicit Deny Overrides Explicit Allow:
Policy Evaluation Order:
User Policy vs. Group Policy:
Explicit Allow in a Policy:
Implicit Deny:
Types of policies
Managed Policies
AWS Managed Policies: These are policies created and managed by AWS. You can attach these policies to multiple users, groups, or roles in your AWS account.
IAM Image
Customer Managed Policies: These are policies that you create and manage. You can attach them to multiple users, groups, or roles in your AWS account.
IAM Image
Inline Policies
These are policies that you create and manage directly within a user, group, or role. Unlike managed policies, inline policies are embedded directly into the resource's definition and are deleted when the resource is deleted. Policies, whether managed or inline, define the permissions for identities (users, groups, or roles) in AWS, specifying what actions are allowed or denied on what resources.
IAM Users
An IAM user is the principal identity in IAM. Each user possesses their own set of credentials, including access keys. Users serve as a means of long-term access to AWS resources, enabling human access to the AWS Cloud through the console. Additionally, they can be utilized by applications to access resources via the access that you can create after the user creation process.
Example of creating a user to access AWS S3 via the CLI:
1: Create a user through the AWS console
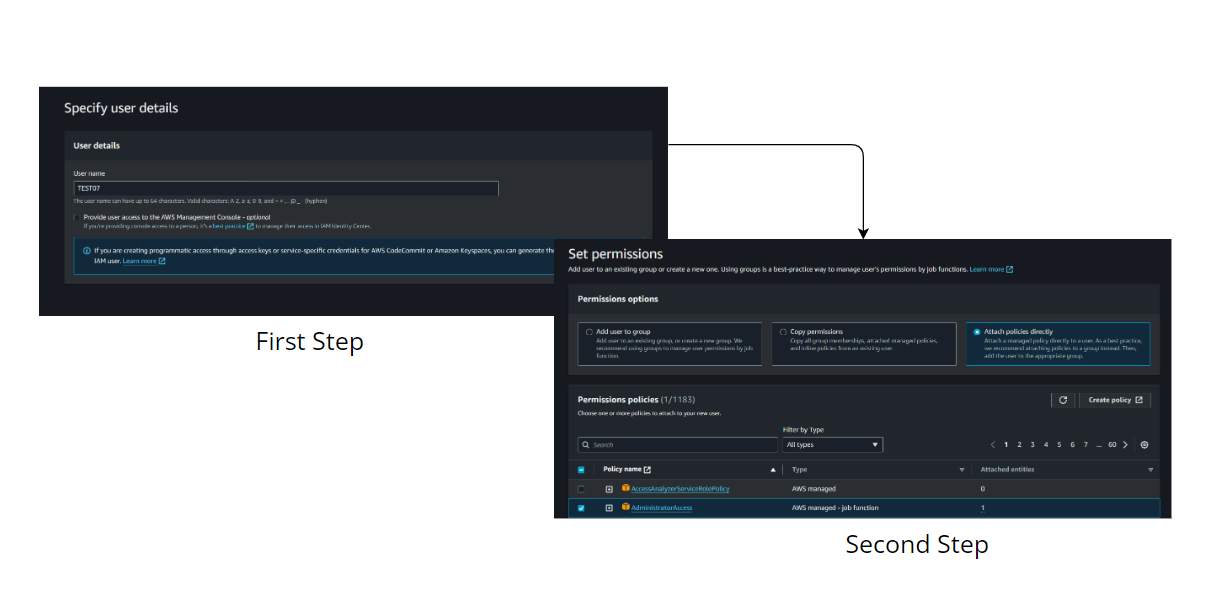
IAM Image
2: Create Access Keys for the user
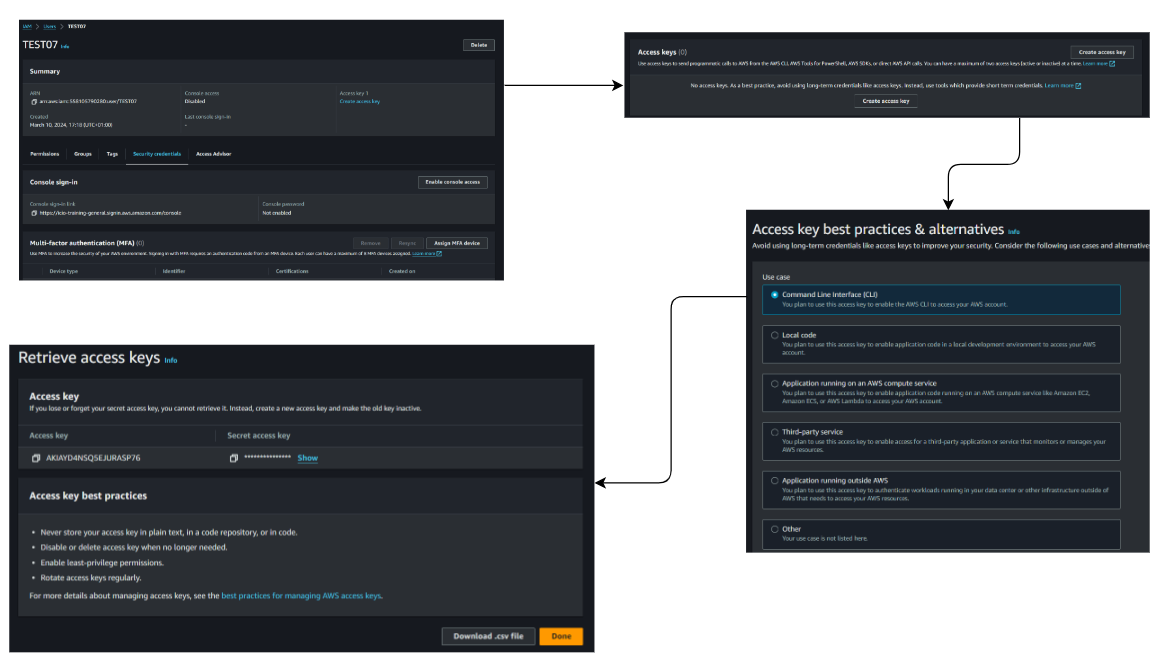
IAM Image
Then install the AWS CLI on your machine if it's not already installed and open a Terminal or Command Prompt and type the following command and press Enter
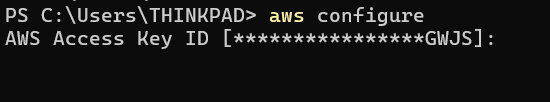
IAM Image
You'll be prompted to enter your AWS Access Key ID and Secret Access Key and specify the AWS region you want to use as the default. Enter the code for your preferred region (e.g., us-east-1).
After entering all information, the AWS CLI will display a message indicating that the configuration was successful.
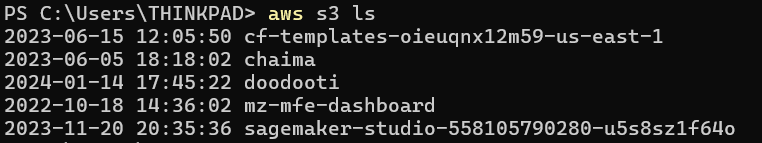
IAM Image
There is a hard limit of 5000 users per account. To overcome this limitation, IAM roles come into play as another type of identity.
IAM Roles
IAM roles in AWS (Identity and Access Management) are a way to grant permissions to entities that you trust. Roles are not associated with a specific user or group; instead, they are assumed by trusted entities, such as AWS services, applications, or users from other AWS accounts.
Key points about IAM Roles
Purpose: Roles are used to delegate permissions, allowing entities to perform actions in your AWS account on your behalf.
Temporary Credentials: When a role is assumed, it provides temporary security credentials, including an access key, secret key, and session token. These credentials are used to make AWS service API requests.
Cross-Account Access: Roles are commonly used for cross-account access, enabling users or services in one AWS account to access resources in another account.
Service Roles: Roles can be assumed by AWS services. For example, an EC2 instance can assume a role to access other AWS services securely.
Trust Policy: A role has a trust policy that specifies who can assume the role. It defines the trusted entities (AWS accounts, IAM users, or AWS services) that are allowed to assume the role.
Permissions Policy: The role also has an associated permissions policy that defines the actions allowed or denied when someone assumes the role.
Here's an example of a trust policy for a role:
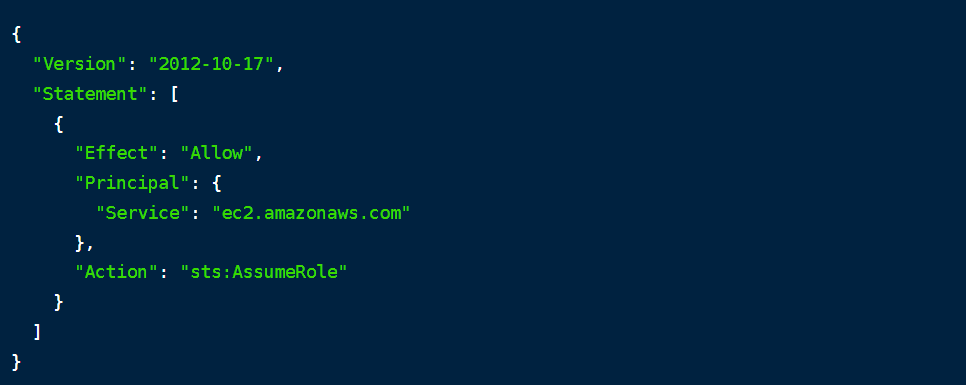
IAM Image
Roles provide a secure and flexible way to manage access to AWS resources, especially in scenarios involving third-party applications, cross-account access, and temporary permissions.
IAM Groups
A group is a collection of IAM users. Groups let you specify permissions for multiple users, which can make it easier to manage access in your AWS environment. Instead of attaching policies to individual users, you can attach policies to a group, and users added to that group inherit the permissions.
Key points about IAM Groups
User Management: users can be added to multiple groups, and each group can have different policies attached, allowing for flexible access management. When a user is added to a group, they inherit the permissions assigned to that group.
Policy Attachment: policies are attached directly to groups, and users in the group inherit those policies. This helps in applying a set of permissions consistently to multiple users.
Simplifies Access Management: group membership simplifies access management, especially when dealing with a large number of users who require similar permissions.
No Credentials: a group itself doesn't have credentials or access keys so you can't login to AWS account via a specific group. Users within the group have their own credentials.
Policy Inheritance: users inherit the permissions of all the groups they belong to, as well as any individual policies that are attached directly to the user. IAM groups are a fundamental component of IAM that helps in organizing and managing user permissions efficiently in AWS.
